From the End, to the Beginning
Well, as per the last post I’m now documenting my journey of development a bit more publicly now. In this case I have deleted my original TryHackMe account and have started again from scratch.
At this point I will do what I can on the free learning items, but inevitably I will need to pay for a subscription. The aim is to use this site and document progress concurrently along with my studies of the eJPT INE course. Naturally I’m not going to copy and paste solutions, but will likely write about the thinking that went into solving the challenges at hand.
Over time I suspect as I become confident with the tools and methodology, I will move onto other sites and challenges as well. But for now, THM and INE are the main focus.
Starting out, I’m using a pre-made Kali Linux image to connect to the lab environments on Try Hack Me. You can download them here, selecting whichever virtual machine platform. In my case I use VMware. It should be noted that when you start your pre-made image up for the first time, make sure that you run updates and upgrades on this before trying to use the features. You can do this with the following commands:
sudo apt-get update && apt-get upgrade
If you haven’t subscribed to Try Hack Me or prefer to connect to their environment using OpenVPN on your virtual machine, I’d suggest starting with this room: https://tryhackme.com/room/openvpn. You may find that you have trouble connecting when first setting up. Before you go to the troubleshooting page, I’d strongly suggest checking that you are typing the commands correctly. Remember, if you’re using Linux Terminal, it is case sensitive, unlike Windows Command Prompt.
Before I start any of the ‘paths’ on this site, I’m going to make the effort to go through the Practice section and focus on learning about the tools. The first on my list is Nmap.
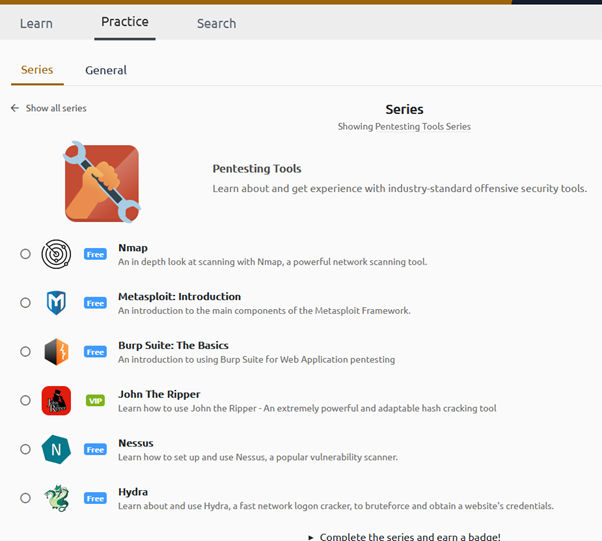
It’s free and already comes pre-installed on Kali. Although I will document some of these items in more detail, the reality is that it won’t sink in until I’m using it. I won’t give a blow-by-blow account of the tutorials, but will likely give a brief overview where I feel it’s necessary.
The main reason I feel I should go through the tool paths first is that a lot of the courses on here, including the introductory ones, expect you to have dabbled with them already. As mentioned in my previous blog, if you don’t have some basic knowledge of the tools, you will find yourself getting stuck and going down rabbit holes. This in turn can lead you to accumulating a list of unfinished courses. This is in turn leads to a lack of focus and hence, a lack of progress.
Being Relevant and Staying the Course
So for now, my approach to learning about penetration testing will be broken down into the following activities:
-
- Practical: Learning about tools directly, using THM and Portswigger to provide a foundation level understanding. At some point I would need to branch off into the tool’s own vendor learning resources for deep dive learning, but for now I want to keep it simple.
-
- Theoretical: Reading up on the theory behind how certain technologies work and why. As foundation guide I will be reading on CompTIA Security+ literature (not sure I want or need the cert), as well from vendors such as Microsoft, Palo Alto etc. Ideally this would be to apply what I learn, but sometimes in order to know how to use tools well, you need to understand what it’s interacting with.
-
- Academic: Mixture of the above. This is for the time I would spend pursuing an actual certification, such as the eJPT or OSCP.
I’ve also been giving more thought about how to stay relevant in my current cybersecurity profession, while at the same time looking to apply that knowledge to penetration testing. The best I could come up with at the moment, is to better understand how to hack cloud platforms. Particularly Azure and AWS. This would give me the excuse to not only learn the security and automation features needed to defend the platforms, but give my subversive imagination a target to engage with.
Admittedly I am still working on how to best approach this. Although there aren’t a shortage of learning materials, cloud platforms are financially risky services to experiment with, even at a free tier level. Created a few VMs and forgot to switch them off? Enjoying getting billed. Hard.
